.png?width=1440&height=840&name=Rectangle%201%20(1).png)
Encryption Solutions
PROTECT DATA AT REST
Secure mission data on devices operating on the edge with Cigent data protection hardware and software. Cigent provides layered CSfC for DAR protection to secure data on PCs, servers, manned and unmanned vehicles, and industrial control systems (ICS).
Trusted By













About
Layered Data Protection
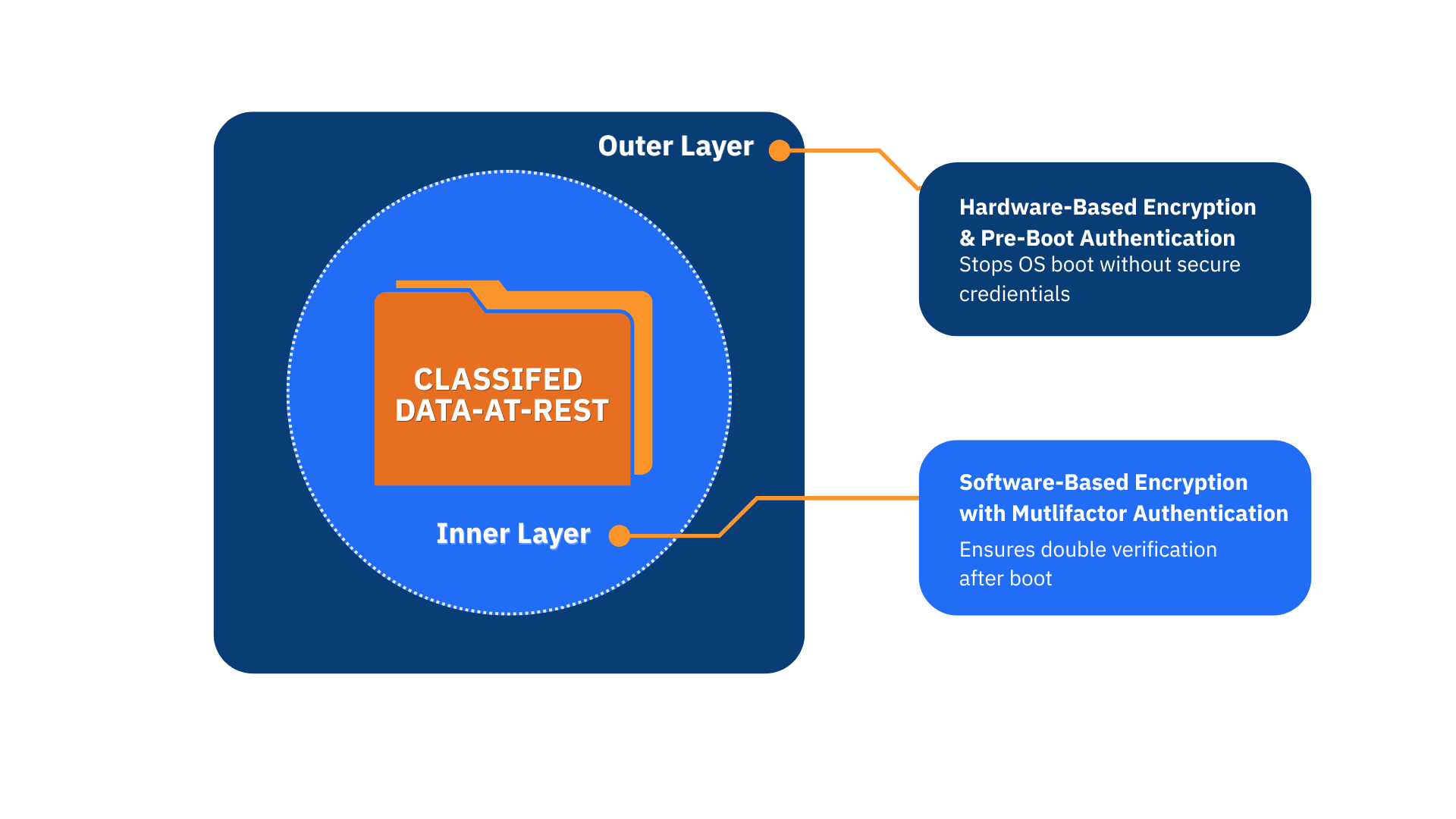
Data at rest on devices operating at the edge is vulnerable. Cigent portfolio of certified drives and software enables organizations to protect sensitive data and meet NSA CSfC data at rest inner and outer layer protection requirements.


Secure Storage
Portfolio of SSDs with AES-256 bit full drive hardware encryption and advanced firmware protection.

Pre-boot Authentication
Pre-boot authentication provides a secure environment to authenticate SSD providing outer protection layer.

Full Drive Encryption
Software full drive encryption provides a separate inner layer of protection with multi-factor authentication.

NSA CSfC for Data at Rest
Cigent solutions address all NSA CSfC requirements. Source all components from Cigent or utilize Cigent software with storage partner including Digistor.
NSA CSfC requires layered security to protect data at rest.
Outer Layer
Comprised of hardware full drive encryption with pre-boot authentication.
Inner layer
Comprised of software full drive encryption with multi-factor authentication.
test and validated by leading Federal Agencies - NSA, NIAP, FIPS 140-2, DISA, and CSfC for DAR, among others.






Cigent Benefits
Device Coverage
Cigent SSDs and software solutions protect PCs, Servers, Manned and Unmanned Vehicles, IoT, and Industrial Control Systems.

Multi Drive Support
Cigent SSDs and software support Workstations and Servers including in RAID environments.
Efficient Management
Command Line Interface (CLI) seamlessly integrates within existing management providing efficient administration at scale.

Efficient Procurement
Cigent drives and software is available through leading device OEMs including Dell, HP, Getac, and Panasonic.
Praise for Cigent

Teresa Shea
Former Director Signals Intelligence NSA
Project Manager in the Intel Community

How We Help
Advanced Threat Protection
.png)
The Cigent Advantage
Cigent solutions were designed and developed with and for US Intelligence and Defense communities. All employees, including Cigent software development, are based in the US. The team includes multiple personnel with TS/SCI clearance with decades of data protection and operational experience to support your requirements.
Cigent solutions have been tested and validated by leading Federal agencies including MITRE, NIST, NSA, NIAP, the Air Force, Cyber Resilience of Weapon Systems (CROWS), and NSSIF (UK) and are deployed across US Intelligence agencies, US Defense services, and the defense industrial base.

ebook
Discover Secure Storage Solutions
Cigent is prepared to support your mission navigating the complex compliance requirements to protect data at the edge. Its solutions were developed for and with US Federal agencies with deep expertise in data protection. Read our extensive eBook to learn more.

ebook
Protect Your Data at Rest
Cigent provides an unparalleled breadth of storage drives with hardware-based encryption enabling operators to achieve compliance mandates and ensure data remains protected in any environment.

Cigent PBA 2.0 Achieves NIAP Listing and CC Certification, Advancing Pre-Boot Authentication for CSfC DAR Protection
New Executive Leadership and Purpose-Built Software Drive Growing Demand for Secure ..

Strengthening Data at Rest Protections: Lessons from Recent Espionage Cases
Strengthening Data at Rest Protections: Lessons from Recent Espionage Cases

Cigent Announces New CEO and Introduces Software Full Drive Encryption Designed for CSfC Compliance
New Executive Leadership and Purpose-Built Software Drive Growing Demand for Secure ..
Frequently Asked Questions
Frequently asked questions ordered by popularity.
Cigent protects data on devices operating at the edge from unauthorized access. Cigent solutions secures data at rest with layered protection including hardware encryption, pre-boot authentication, and multifactor authentication. Cigent also ensures data integrity when the device is in use preventing wiping and cloning and other data attacks.
To prevent sophisticated adversaries from unauthorized access requires layered protection. The foundation of Cigent solution is 256-AES full drive hardware encryption with pre-boot and multifactor authentication. These capabilities have been validated by agencies including NSA and NIAP. Additionally, Cigent provides capabilities that ensure the integrity of data through its lifecycle including hidden partitions, storage-embedded AI, and verified data erasure.
Data at rest encryption traditionally refers to the encryption of data when the device is asleep or powered-off. Data at rest encryption seeks to prevent adversaries who gain physical access to the device would seek to extract sensitive data. Cigent uses AES 256 full drive hardware encryption with pre-boot and multifactor authentication. In addition, Cigent uses zero-trust access to control to also protect data when a device is in use. This is with hidden partitions that maintain encryption until it is accessed with step-up authentication.
Cigent provides the widest breadth of secure storage solutions all utilizing hardware encryption. These includes: PCs supporting both M.2 2280 and the emerging M.2 2230 standard, remote servers and NAS devices with U.2 drives, external media with flash drives, encrypted external drives, SD and Micro SD cards, and embedded for SSD BGA.
Yes, Cigent Secure Storage Solutions can support organizations meeting Commercial Solutions for Classified (CSfC) for data at rest including pre-boot authentication requirements. Cigent solutions can also meet FIPS 140-2 and 140-3 standards. Additionally, Cigent can address requirements from Executive Order 14028 including encryption of data at rest, multi-factor authentication, and the utilization of zero-trust access control. Cigent protections have been thoroughly tested and validated by leading Federal agencies including MITRE, NIST, NSA, NIAP, the Air Force, Cyber Resilience of Weapon Systems (CROWS), and NSSIF (UK).
Still have questions?
Learn more about Cigent and our solutions by downloading our company overview.

Cigent Partners
Cigent partners with some of the top manufacturers and firms.
.png?width=300&height=100&name=Untitled%20design%20(3).png)

© 2025 Cigent Technology Inc.




